Federal Trade Commission (FTC) Alert
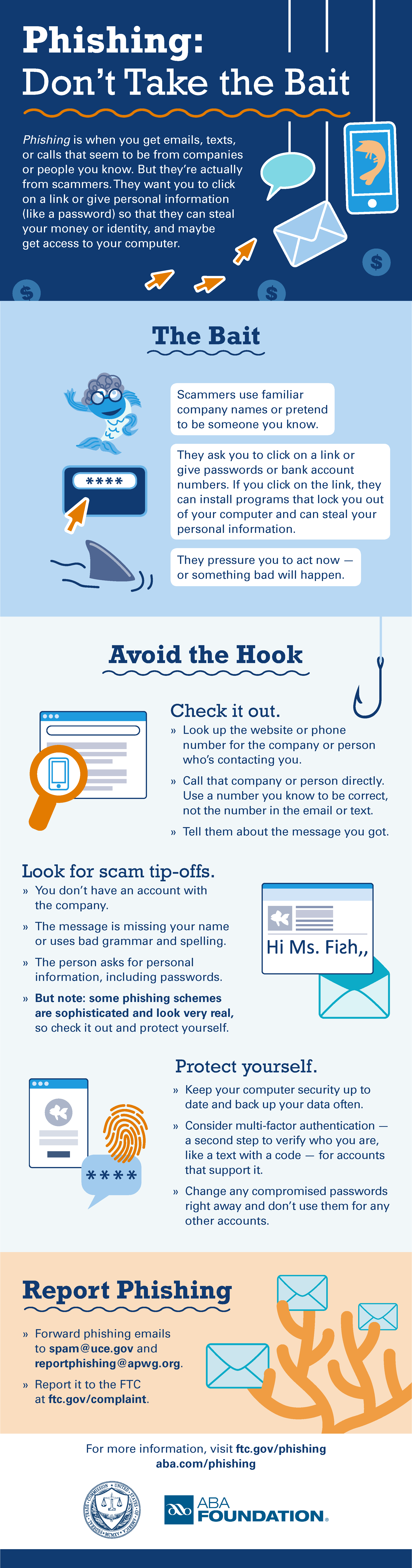
Phishing is when a scammer uses fraudulent emails or texts, or copycat websites to get you to share valuable personal information – such as account numbers, Social Security numbers, or your login IDs and passwords. Scammers use your information to steal your money or your identity or both.
Scammers also use phishing emails to get access to your computer or network then they install programs like ransomware that can lock you out of important files on your computer.
Phishing scammers lure their targets into a false sense of security by spoofing the familiar, trusted logos of established, legitimate companies. Or they pretend to be a friend or family member.
Phishing scammers make it seem like they need your information or someone else’s, quickly – or something bad will happen. They might say your account will be frozen, you’ll fail to get a tax refund, your boss will get mad, even that a family member will be hurt or you could be arrested. They tell lies to get to you to give them information.
Be cautious about opening attachments or clicking on links in emails. Even your friend or family members’ accounts could be hacked. Files and links can contain malware that can weaken your computer's security.
Do your own typing. If a company or organization you know sends you a link or phone number, don’t click. Use your favorite search engine to look up the website or phone number yourself. Even though a link or phone number in an email may look like the real deal, scammers can hide the true destination.
Make the call if you’re not sure. Do not respond to any emails that request personal or financial information. Phishers use pressure tactics and prey on fear. If you think a company, friend or family member really does need personal information from you, pick up the phone and call them yourself using the number on their website or in your address book, not the one in the email.
Turn on two-factor authentication. For accounts that support it, two-factor authentication requires both your password and an additional piece of information to log in to your account. The second piece could be a code sent to your phone, or a random number generated by an app or a token. This protects your account even if your password is compromised. As an extra precaution, you may want to choose more than one type of second authentication (e.g. a PIN) in case your primary method (such as a phone) is unavailable.
Back up your files to an external hard drive or cloud storage. Back up your files regularly to protect yourself against viruses or a ransomware attack. Keep your security up to date. Use security software you trust, and make sure you set it to update automatically.
Report phishing emails and texts.
Forward phishing emails to spam@uce.gov (Opens in a new Window) – and to the organization impersonated in the email. Your report is most effective when you include the full email header, but most email programs hide this information. To ensure the header is included, search the name of your email service with “full email header” into your favorite search engine.
File a report with the Federal Trade Commission at FTC.gov/complaint (Opens in a new Window).
Visit Identitytheft.gov (Opens in a new Window). Victims of phishing could become victims of identity theft; there are steps you can take to minimize your risk.
You can also report phishing email to reportphishing@apwg.org (Opens in a new Window). The Anti-Phishing Working Group – which includes ISPs, security vendors, financial institutions and law enforcement agencies – uses these reports to fight phishing.
Identity Theft
Identity theft happens when someone uses your Social Security number or other personal information to open new accounts, make purchases, or get a tax refund.
Most people who experience identity theft must take several steps to recover. IdentityTheft.gov (Opens in a new Window) is the federal government’s one-stop resource to help you report and recover from identity theft. The site provides step-by-step advice and helpful resources like easy-to-print checklists and sample letters.
If you believe that someone is using your personal information, visit IdentityTheft.gov (Opens in a new Window).
Warning Signs
There are many ways that you might discover that someone is using your information. You might get a notice from the IRS or find unfamiliar accounts on your credit report. You might notice strange withdrawals from your bank account, get bills that aren’t yours, or get calls about debts that you don’t owe.
What To Do Right Away
If you see one of these warning signs of identity theft, act quickly. Taking these steps will help you limit the damage. IdentityTheft.gov (Opens in a new Window) will guide you through each step.
- Call the companies where you know fraud occurred.
- Place a fraud alert on your credit reports and get copies of your report.
- Report identity theft to the FTC (Opens in a new Window).
- File a report with your local police department.
- Then, take a deep breath and begin to repair the damage. Depending on your situation, your next step might be closing accounts opened in your name, or reporting fraudulent charges to your credit card company. IdentityTheft.gov (Opens in a new Window) can help — no matter what your specific identity theft situation is.
If Your Info Is Lost or Stolen
Did you recently get a notice that says your personal information was exposed in a data breach? Did you lose your wallet? Or learn that an online account was hacked? Depending on what information was lost, there are steps you can take to help protect yourself from identity theft.
Protecting Your Identity
While identity theft can happen to anyone, there are some things you can do to reduce your risk.
Here are five ways to make protecting your identity part of your everyday routine:
- Read your credit card and bank statements carefully and often.
- Know your payment due dates. If a bill doesn't show up when you expect it, look into it.
- Read the statements from your health insurance plan. Make sure the claims paid match the care you got.
- Shred any documents (Opens in a new Window) with personal and financial information.
- Review each of your three credit reports at least once a year. Visit annualcreditreport.com (Opens in a new Window) to get your free reports.
For more prevention tips — and resources you can share with others — visit ftc.gov/idtheft (Opens in a new Window).